For a more moral world, support open-source software based programs and file sharing--by using them. No one should own the very language or infrastructure through which we communicate. Otherwise, you get this: state spying apparatuses dominating the design and funding of Facebook, Google, and Microsoft Windows.
That's OK, you might say, I'll stick to Apple products. However, the CIA seems to have had a close relationship as a tailored "niche customer" (previous author's words) with Steve Jobs's NeXT Computer (early 1990s); then the Pentagon had contracts with Apple under Steve Jobs. Steve Jobs even had a top secret clearance from 1988-1990 according to the uncensored sections of his recently released (and thus only partially released) FBI file. Documentation on this below.
How extensive are these monopoly websites in their use for monitoring, conditioning, and curtailing behavior instead of merely facilitating it? The data is from a section in the BBC's Virtual Revolution, a 4-part documentary produced in 2010 on the informational revolution. Here's a representation of the scale and geographic location of the informational society from that documentary:

Of the United Kingdom's 60 million people, 35 million log onto the web daily. From a unique sample of 8 million of these people in 2009 by Experion Hitwise, this a mathematically accurate map of this uneven world and where people go: "dominated by a handful of megabrands...that can impose their brands and their authority."

THE TWO LARGEST monopoly areas of web universe were funded by U.S. intelligence services. It would be the three largest monopoly areas of the web if you count that most people view the Internet through a near monopoly on web browsers and personal computer architecture dominated by Microsoft Windows--a US-state-supported monopoly that they refuse to break apart despite it being against U.S. trust legislation to ignore it. All three have spy connections. Combined, this incredible extension of secret jurisdictional monitoring in our lives worldwide bodes badly for the software industry and for regular communication and information access.
There is additional evidence that a fourth area, Steve Jobs and Apple Computer, now one of the financially richest, largest merged software/hardware companies in the world as of 2012, had Pentagon connections since 2001. NeXT Computer (a company Steve Jobs founded after he was fired from Apple in the 1980's for being such a self-destructive psychopath in that previous company) had CIA connections. More on that below as well.
This state-funded creation of monopolies in communication software via Google, Facebook, and Microsoft Windows endangers personal privacy and civil liberties. When personal privacy is endangered, civil liberties are endangered. And when civil liberties are endangered, it is a quick (goose)step toward democratic demotion and open tyranny. It additionally curtails information flow as Google (which is Blogger and YouTube as well) works with states worldwide to censor web output from its search engine or its databases without its users awareness that certain information has been actively 'disappeared' instead of passively 'does not exist'--actively hidden from particular countries' searchings of the web.
The solution is to maintain privacy in policy and via a wide ecology of non-proprietary software. These are two novel checks and balances for the Ecological Reformation--extension requirements for democracy in the informational and knowledge areas of our lives for sustainability. (Avoiding corrupting monopolies via maintaining a wide ecology of market choices for consumers apply to all other commodity ecology choices as well.)
Without these two important changed features of the online world, real world democracy has been demoted toward a police state that has created an online surveillance society via these state-supported corporate monopolies.
How much of a concern is this? And what are the specific links to spycraft of these three monopolies? Let's look at some statistics and pictures of statistics now.
As of 2010, there is a website that tells its users it openly shares all of their private account data with others outside of the company, without their permission or even acknowledging they are doing so. Of the WHOLE world's Internet users, 30% give personal information to this private website.
By 2010 in the USA 77% of its population reported personal information on the same private website on a regular basis. By 2010, this means that this website has over 500 million files globally. It has knowledge of personal beliefs and friendship networks updated in real time accessed by private owners who share it with anyone they choose.
Thus by 2010, this private website was larger than almost all countries of the world--except for two. How soon until this one private website database IS the largest country, the largest people surveillance database in the world?
That website is Facebook.com. Facebook was built into an empire with funding from the U.S. intelligence community via In-Q-Tel (set up by the CIA) and with other funding from the military directly like U.S. Defense Department via other funding sources connected to DARPA's goals. Thus Mark Zuckerberg's Facebook empire was made into an empire by the CIA and the U.S. Defense Department, in other words, to serve state ends. As they say, follow the money:
Facebook - CIA Profile Database
by Vishal Agarwala
4:00 min
Microsoft
Let's turn to Microsoft Windows, the monopoly for information architecture built into personal computing and the web. As of October 2009, Windows had approximately 91% of the market share of the client operating systems for usage on the Internet and 43% of the web browsers. This means almost all of the personal computers worldwide experience a Microsoft machine and almost half experience a Microsoft web. Microsoft has a very hard-nosed 'proprietary' (i.e., secret) set of rules around Microsoft Windows software use and refuses to share its code for examination.
Microsoft's bundling of its components pre-sale on hardware or designing components to fail to work openly with a user's choice of software outside of Microsoft is legion. On April 3, 2000, a judgment was handed down in the case of United States v. Microsoft, calling the company an "abusive monopoly"; it settled with the U.S. Department of Justice in 2004. In 2001 the company released the Xbox, entering the game console market dominated by Sony and Nintendo. In March 2004 the European Union brought antitrust legal action against the company, citing it abused its dominance with the Windows OS, resulting in a judgment of €497 million ($613 million) and to produce new versions of Windows XP without Windows Media Player, Windows XP Home Edition N and Windows XP Professional N.
News from 2010 shows that the NSA (the 'electronic signals intelligence' branch of the military) is now openly working with Microsoft Corporation. This means the NSA liases with and depends upon a global monopoly on personal computer architecture and web experience. I find it suspicious that the well publicized U.S. government attempt to remove this monopoly in the courts entirely disappeared. Instead, the U.S. intervened to keep the Microsoft monopoly from being dismantled as illegal. Perhaps the massive NSA spying framework was a major rationale for allowing the illegal monopoly of Bill Gates to continue? Wayne Madsen related that there's even a person at the NSA responsible for liasing with the monopoly of Microsoft. Madsen additionally brings up the 'NSAkey' discoveries in previous versions of Windows' code:
NSA Could Be Looking Through Your Windows
4:01 min
Let's turn to Google. What about the equally quick growth of the monopoly of Google? Google.com was built into an empire from the same U.S. intelligence money, from three different sources. One of them was In-Q-Tel--the U.S. intelligence apparatus funder that built Facebook as well. The other two were Kleiner Perkins and Sequoia Capital. Both of these other two original funders were highly inbred with the U.S. military. Floyd Kvamme, partner of Kleiner Perkins venture capital firm that funded Google. Floyd Kvamme was appointed by George W. Bush as a co-chair of the Bush Administrations technical advisory group. His son, Mark Kvamme was partner of Sequoia Capital that funded Google as well. Mark Kvamme had direct meetings with the U.S. Secretary of Defense Donald Rumsfeld. (Meanwhile, Sequoia Capital has funded several other startup corporations that were contracted immediately to fulfill U.S. Defense Department/Pentagon desires once created. To solidify the links, a partner of Kleiner Perkins, John Doerr, was placed as a director of Google. A partner of Sequoia Capital, Michael Moritz, was placed as another director of Google.
Meanwhile, the international press provides distraction: it talks incessantly about the Google corporation's youthful multi-billionaire front men, Larry Paige and Sergey Brin, instead of talking about the three deep U.S. intelligence connections that built Google--connections directly into the U.S. intelligence and military.
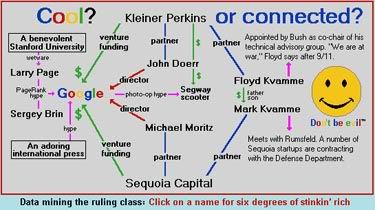
More information: namebase.org to follow the links
Furthermore, Webster Tarpley notes that despite Google's 'eyewash' image to the contrary, it has always liased with U.S. spies--particularly how the CIA's Project Keyhole (a global surveillance grid of the Earth) was given to Google to develop into Google Earth which conveniently has user data for what people look at, passed along as personal information. And now from 2010 Google openly liaises with the NSA like the open relationship between NSA and Microsoft designing software, just like Google has a history of developing once top secret CIA projects into technology applications like Google Earth.
Google has been accused by Tarpley of censoring the speech of political activists--exactly what Facebook did in September 2010 with wide Facebook-organized boycotts against Target Corporation or BP. Facebook simply 'deleted' the organizing tool for the activists, and banned their organizing administrators from posting.
In short, these massive tools on the web are in practice instruments of spycraft and censorship instead of only information delivery services.
NSA and Google Are Partnering Up
4:37 min
So why believe or give Google the benefit of the doubt when they say they 'accidentally' gathered wireless internet information from their Google Vans worldwide. No one should believe them because Google Earth itself was a CIA idea (Project Keyhole) given to Google to administrate and three other main funders all had open U.S. intelligence connections:
Scandal: Google Gathering "SigInt" (signals intelligence) in its Google Vans for Google Earth, Who Gets the Data?
5:37 min
Third, similar to the Nazi Third Reich's police biological databases on the population (that organized murder of millions of individuals based on centralized knowledge of demographic/ethnic heritage information), Google's "Master Plan" is to link Google data with your DNA via biometric data and your medical records. If, Google's Master Plan is to connect its data to your genetics, can someone say "Fourth Reich in the making"? Europe's strong data protection laws reflect real world concern about this centralized knowledge because they have historical experience of what ideological psychopaths do with such knowledge: ethnic cleansing and police state operation. This destroys representative democracy which is unsustainable behavior:
Google's Master Plan
3:13 min
Apple
Below is a verbatim article written after Steve Jobs's death, by Sashi Sri Kantha in October 22, 2011, entitled "Steve Jobs: A Smartly Hidden Angle":
Steve Jobs (1955-2011)
A Smartly Hidden Angle
by Sachi Sri Kantha, October 22, 2011
Can anyone argue that Steve Jobs was working with Pentagon to support Mother Teresa’s life work as objectives? Pentagon’s current budget request for fiscal year 2012 is a whopping $671 billion, as Pentagon is seeking mini-weapons for new age of warfare, according to W.J. Hennigan [Los Angeles Times, May 30, 2011]. By omission, the main stream media’s scribes have smartly hidden Steve Jobs’s penchant as bomb designer.
Since the death of computer industry tycoon Steve Jobs on October 5, hundreds of headlines, editorials, cover stories and eulogies have appeared. Mine will be different. I provide a critical angle which these sob stories have completely omitted or muted. So, I play the devil’s advocate here.
Not a single item over ten representative samples from leading print media icons that I have read about Jobs’s career profile [see below the sources I cite] provide information about how much of Pentagon funds landed into Apple company’s research programs for mini weapons, since Sept.11, 2001. Mind you that these mini weapons are Pentagon’s play toys for death, injury and property destruction. I like this euphemistic four-word cliche which two American presidents have been using for the past ten years: ‘Bring him (them) to justice’, which literally means ‘to kill’(not only Saddam Husseins and Osama bin Ladens). This is a blanket clause to kill hundreds of thousands of human lives as collateral damage, courtesy the bombs and accessories designed from Jobs’s computers and other secretly contracted weapons.
CIA was a niche customer for the NeXT computer
There is no question that Jobs was a designer par excellence. By all accounts, he was ‘addicted’ to secrecy. I also read one of the biographies of Steve Jobs; that of Leander Kahney entitled ‘Inside Steve’s Brain’(2008). In the blurb, Leander Kahney is introduced as a news editor for Wired.com, and “as a reporter and editor, Kahney has covered Apple for more than a dozen years”. In it, there is a passing mention in one sentence of the introduction, that the NeXT computer which Jobs made after he was fired from the Apple in 1985, had the CIA as one its niche customers! [editor's note: "Niche customer" seems to be an understatement: NeXT Computers were designed with the CIA in mind, because the CIA was the largest buyer of these NeXT computers:]
INSET FROM Wired.com:
1.06 - Jun 1993
1.06: Street Cred
Now we know who bought NeXT computers: The CIA and other spooks were the company's biggest customers, says Randall Stross in [the book] Steve Jobs and the NeXT Big Thing. [reviewed here:]
Issue 1.06 | Dec 1993
Steve Jobs and the NeXT Big Thing
By Phil Patton
Now we know who bought NeXT computers: The CIA and other spooks were the company's biggest customers, says Randall Stross in Steve Jobs and the NeXT Big Thing. It's a neat irony, the black-bag boys buying into the black box, but not too useful when it comes to customer testimonials.
Stross is a professor of business, and he tells the story of NeXT, the business. With its Reality Distortion Field of Dreams marketing, the company ran through some US$250 million of capital to sell just 50,000 computers.
(Steve Jobs and and the NeXT machine: brilliant, charming, but with no input jacks.)
But NeXT was more than a business story. It was a story of celebrity, hype, and technological folklore. Hartmut Esslinger of frogdesign designed the cube, he said, to represent "revenge" - Jobs's desired revenge against Apple. But Stross makes one error: NeXT's magnesium box, so expensive to cast and paint, was not in fact a perfect cube. One side was slightly larger. Nothing at NeXT was quite as it appeared - sales figures, for example, were constantly inflated.
The black box was a perfect metaphor for the enterprise: a piece of minimalist art into which the viewer could project his or her own imaginings. One such projecter was investor Ross Perot, who said wistfully, "These kids remind me of when I was young." (After reading the details here, American citizens may think more carefully about any enterprise Perot backs.)
As Alan Kay told me, at the time the cube was introduced, both the first Mac and NeXT were like models of Steve's head: brilliant, charming, but with no input jacks. But however much NeXT was a reflection of Jobs's legend and his flaws, those of us who covered NeXT or rooted for it were in a sense complicitous in the failed enterprise.
People wanted to believe that there was indeed a next big thing, rather than a future of small steady enhancements, refusing to accept that the revolution had slowed down to evolution.
Steve Jobs and the NeXT Big Thing, by Randall Stross, US$24. Atheneum.
---
http://www.wired.com/wired/archive//1.06/streetcred.html?pg=8&person=steve_jobs&topic_set=wiredpeople
BACK TO STEVE JOBS:
And I also quote two paragraphs from this book, which alludes to CIA style obsession to secrecy. Again, CIA is passingly mentioned.
“Jobs’s Apple is obsessively secretive. It’s almost as secretive as a covert government agency. Like CIA operatives, Apple employees won’t talk about what they do, even with their closest confidants: wives, boyfriends, parents. Employees certainly will not discuss their work with outsiders. Many won’t even refer to the company by name. Like superstitious theater folk who call Macbeth the ‘Scottish play’, some Apple employees call it ‘the fruit company’.
Talking out of school is a firing offense. But many employees don’t know anything anyway. Apple staffers are given information on a strictly need-to-know basis. Programmers write software for products they’ve never seen. One group of engineers designs a power supply for a new product, while another group works on the screen. Neither group gets to see the final design. The company has a cell structure, each group isolated from the other, like a spy agency or a terrorist organization.” (pp. 140-141).
By design or accident, the CIA is not mentioned in the index of this book [despite being mentioned in the book].
[editors note: In the recent 'thick' biography about Steve Jobs by Walter Isaacson (October 2011), CIA connections openly mentioned in his previous biography are (un)curiously censored out. What kind of author is Isaacson? He seems a shallow one who fails to even note or ask Steve Jobs who bought the majority of his 50,000 NeXT Computers that he sold: the CIA.
In addition to spy agency connections and sales to it via his company NeXT, Steve jobs had actual top secret clearance via his other company PIXAR.
The FBI file of Steve Jobs was recently released. It was redacted/censored instead of released in full so Steve Jobs still has some very sensitive secrets BEYOND what is revealed in it. However, in this redacted FBI file we still learn that after Steve Jobs was fired from Apple (for being divisive and endangering the company's profits, according to his biographer Isaacson) Jobs scored a top secret clearance with U.S. intelligence agencies from 1988-1990 via his work at PIXAR in the same period he was selling the majority of his NeXT computers to the CIA. Quoting
"It’s no secret that Jobs had his fair share of enemies, but to see so many of his supposed “friends” questioning his character [in FBI file interviews about him] is quite surprising. [Another bit]...of information gleamed from this report...: Jobs had Top Secret Security Clearance from 1988 to 1990. There’s no indication as to why he received it, but the agency associated with the clearance was Pixar. UPDATE: As per the site that originally broke this story, Gawker, a source who worked with Jobs stepped forward and emailed the site to say “several people had security clearances at Pixar since, in the early days, they were selling an image rendering software system that could be used to enhance satellite surveillance photographs and film. There was even a Chernobyl demo. They thought that the ‘spooks’ would provide a huge market.”Later Apple-to-Department of Defense connections are missing as well from Isaacson's book about Steve Jobs as well. Third, Isaacson's book raises some other interesting red flags for me, since one of Steve Jobs's closest friend in the book is the CEO of ORACLE, Larry Ellison. And this company was virtually founded by the CIA in 1977:
Full FBI file: http://documentcloud.org/documents/291363-jobs.html
Information and site that originally broke the story: gawker.com/5883670/steve-jobs-fbi-file-released?utm_campaign=socialflow_valleywag_twitter&utm_source=valleywag_twitter&utm_medium=socialflow
"This article in Forbes Magazine notes that Oracle billionaire Larry Ellison worked on a CIA project with the code-name "Oracle": "He [Larry Ellison] dropped out of ..."
www.dba-oracle.com/oracle_news/news_oracle_origin.htm
Oracle's coziness with government goes back to its founding /
"20 May 2002 ... Founded in May 1977, the firm's name came from a CIA project code-named " Oracle." Company co-founders Larry Ellison, Robert Miner and ..."
www.sfgate.com/cgi-bin/article.cgi?f=/c/a/2002/05/20/MN209661.DTL&ao=all
INSET ABOUT ORACLE: CEO, Larry Ellison, in Isaacson's book, comes across one of Steve Job's closest multi-billionaire friends:
WEDNESDAY, JUNE 23, 2010
Oracle's Connection to the CIA
Most Oracle professionals are surprised to learn that the name "Oracle" originates from the name of a CIA project. This article in Forbes Magazine notes that Oracle billionaire Larry Ellison worked on a CIA project with the code-name "Oracle":
"He [Larry Ellison] dropped out of the University of Chicago in the 1960s, headed to Berkeley, Calif. and by the mid-1970s began working on a database project. Code name: Oracle. Client: the Central Intelligence Agency.
In 1977, Ellison founded the company with Robert Miner and Edward Oates, naming it after the CIA job."
http://www.dba-oracle.com/oracle_news/news_oracle_origin.htm
HOW TO TELL ORACLE CORP. FOUNDER LARRY ELLISON FROM GOD
Oracle's coziness with government goes back to its founding / Firm's growth sustained as niche established with federal state agencies
SFGATE.com | May 20, 2002
... Company co-founders Larry Ellison Robert Miner and Ed Oates worked on Project Oracle at a consulting firm before striking out on their own.
A quarter century later close to a quarter of the [ORACLE] company's revenue -- $2. 5 billion a year -- still comes from selling software to federal state and local agencies.
"Oracle wouldn't exist if it weren't for government contracts," said Mike Wilson, author of the book The Difference Between God and Larry Ellison.
Oracle has 1000 sales and consulting workers focused exclusively on government work. And in the wake of Sept. 11 Oracle is counting on the heightened interest in staving off terrorism to boost its government ties even more.
Oracle has been actively pitching software to local governments to create detailed digital maps that could be used to respond to attacks. In March the company formed a partnership to focus on airport security. Ellison even offered to give the federal government software to help create a national ID to thwart terrorists.
In a background paper Oracle boasts that it is "very active in homeland security."
Banc of America Securities analyst Bob Austrian believes the entire high-tech industry could profit from the increased security spending. But he suspects Oracle could do better than most because it already has an unusually large share of government contracts and is in a particularly relevant niche.
"The majority of interest surrounds tracking individuals and information which by its nature is a database-intensive application" he said.
So perhaps it's fitting that Oracle is making headlines because of concerns over the recent $95 million government contract.
Among the allegations are that Oracle persuaded California officials to buy more software than needed misrepresent the costs savings and rush through a no-bid award without considering alternatives. It didn't help that Oracle handed a $25000 check to Gov. Gray Davis' technology adviser just two weeks after the deal was signed.
http://articles.sfgate.com/2002-05-20/news/17546036_1_larry-ellison-robert-miner-homeland-security-government-contracts
---
http://robertscourt.blogspot.com/2010/06/oracles-connection-to-cia.html
BACK TO STEVE JOBS:
Now, will you care to fill in the dots about Steve Jobs: secrecy, designer in chief, comparmentalized design teams on 'need to know basis' only, CIA and Pentagon contracts, and a history of top secret clearances. [And with Steve Jobs's a lifelong friend of Larry Ellison, the latter who got his foot in the door in the technology sector with CIA contracts--and kept his foot in that door as well.] I’d claim that going by President Barack Obama’s high-octane public eulogy, Steve Jobs was also a bomb designer. My clinching proof: the Apple Company was buffeted by lofty work contracts with Uncle Sam’s Pentagon.
Apple’s links to the Pentagon
For those who had missed this item, I provide below in entirety, what I located in the web: a news item by Bryan Chaffin (Executive Vice President), dated March 24, 2010, with the caption ‘U.S. Army visits Apple HQ to discuss military devices’ from The Mac Observer site.[ http://www.macobserver.com/tmo/article/u.s._army_visits_apple_hq_to_discuss_military_devices/]
“The U.S. Army sent representative officers to Apple’s headquarters in Cupertino, CA to, “discuss the use of Apple products in Army business and battlefield operations.” According to a post at the Army’s Web site, the military respects Apple’s technology and products, and is looking to find ways to leverage commercially available technology for its soldiers in the battlefield.
“Apple technologies offer unique and proven solutions with intuitive designs that allow users to learn quickly without a training manual,” Ron Szymanski, CERDEC’s lead computer scientist for the U.S. Army Research, Development and Engineering Command (RDECOM), said in a statement. “The Army would like to leverage Apple’s experience when designing military applications.” More specifically, the Army said it was evaluating the use of the iPad, iPhone, iPod, iMac, and MacBook platforms in a military capacity.
“The Army is moving away from big-green-box solutions and toward those that will adapt along with our warfighters on the battlefield,” Maj. Gen. Nick Justice of RDECOM said. “We’re continuing to leverage commercial technology for battlefield uses; we can’t ignore that kind of existing knowledge. Our job, as stewards of the taxpayer’s dollar, is to adopt and adapt appropriate commercial technology and offer the best possible solution to the warfighter.”
More praise was sent Apple’s way by Dr. Gerardo J. Melendez, director of Command and Control Directorate (CERDEC), a division within RDECOM, who said, “As we push to develop more commercial capabilities to meet Army information and knowledge management needs, it’s important that we engage companies such as Apple because we stand to benefit just as much from their lessons learned and best practices.” He added that the Army could realize cost savings by not always re-inventing the wheel by turning to some of the advanced commercial technology being developed by American technology companies.
An attorney contacted by The Mac Observer noted that above and beyond the potential for Apple to secure lucrative contracts with the U.S. military for developing devices or specializing existing devices for the military’s use, offers other possible benefits to Apple. “If Apple can secure a military contract and the military declares Apple’s device to be essential to U.S. security, the DOJ [could choose to] intervene in the Nokia v. Apple case as an interested party and move the court to stay any adverse ruling against Apple that adversely affects national security and/or move for an order directing Nokia to license the essential technologies on what would be essentially Fair, Reasonable and Non Discriminatory (FRAND) terms, at least for the military’s mobile devices.” All of which may be putting the horse before the cart, as this was just one meeting between the Army and Apple that is being discussed. That said, the Army added that the meeting ended with plans for future technical discussions between the two organizations.”
Can anyone argue that Steve Jobs was working with Pentagon to support Mother Teresa’s life work as objectives? Pentagon’s current budget request for fiscal year 2012 is a whopping $671 billion, as Pentagon is seeking mini-weapons for new age of warfare, according to W.J. Hennigan [Los Angeles Times, May 30, 2011]. By omission, the main stream media’s scribes have smartly hidden Steve Jobs’s penchant as bomb designer.
Stever Jobs - a Secular Prophet ?
I found it somewhat disappointing and discomforting, while reading Andy Crouch’s ‘in depth’ feature entitled ‘The Secular Prophet’. In it, he had compared Jobs’s philosophy of life to that of Socrates, Buddha and Emerson, based on Jobs’s commencement address to the Stanford University students in 2005. Merde, I’d say. I quote the relevant excerpt:
“ ‘No one wants to die. Even people who want to go to heaven don't want to die to get there. And yet death is the destination we all share. No one has ever escaped it. And that is as it should be, because Death is very likely the single best invention of Life. It is Life's change agent. It clears out the old to make way for the new. Right now the new is you, but someday not too long from now, you will gradually become the old and be cleared away. Sorry to be so dramatic, but it is quite true. Your time is limited, so don't waste it living someone else's life. Don't be trapped by dogma which is living with the results of other people's thinking. Don't let the noise of others' opinions drown out your own inner voice. And most important, have the courage to follow your heart and intuition. They somehow already know what you truly want to become.’
This is the gospel of a secular age…Mr.Jobs was by no means the first person to articulate this vision of a meaningful life – Socrates, the Buddha and Emerson come to mind…”
Hey, the life stories of Socrates and Buddha that I read don’t synch with the half-baked interpretation provided by Andy Crouch on Jobs’s life! Socrates wanted to die, to prove that his tormentors were wrong. That’s why he took hemlock voluntarily in 399 BC. But, Steve Jobs preached to the Stanford Students in 2005 that ‘No one wants to die…’Blah! Blah! That death is the ultimate destination is no new stuff either. If Steve Jobs had sacrificed his life like Socrates, rather than undergoing liver transplant, then I’d have applauded him as a worthy successor of Socrates. Unlike Steve Jobs, Socrates never bothered to capture the world market in digital electronics to become rich. Lord Buddha, renounced everything (his kingdom, family, and material wealth) to preach his Gospel. Did Steve Jobs renounce his family and material wealth to preach his Gospel?
The Magician
The Economist magazine [Oct.8, 2011] featured Steve Jobs on its cover with the caption ‘The magician’. In its original sense of the word, a magician creates illusions. Thus, I agree with this adjective. Jobs had the uncanny ability to pick the pockets of American taxpayers directly and indirectly; directly, by his designed end products Apple computers, ipods, itunes, iphones, ipads etc.: indirectly, by landing lofty work contracts from Pentagon, which gets its funds solely from American taxpayer. But, I’m not so naive to tag him with superlatives such as ‘visionary’, ‘genius’, ‘prophet’ etc. Of course, there are other Pentagon contractors. But they don’t sell helicopters, nuclear submarines and aircraft carriers to average John and Jane. In sum, Steve Jobs was a sweet talking, smart entrepreneur of illusions.
What rankles me is that there is a fine line which separates a bomb designer and a terrorist. The mainstream international media and the pundits of U.S. State Department tagged Velupillai Prabhakaran as a terrorist, merely because he ‘designed’ suicide bombs. So, how about Steve Jobs? Available public evidence indicates that he also was a bomb designer in a figurative sense. So, why he is not tagged as a ‘terrorist’?
Cited Sources
Anonymous: The magician: the revolution that Steve Jobs led is only just beginning [Leader item]. Economist, Oct.8, 2011, p.15.
Anonymous: A genius departs. Economist, Oct.8, 2011, pp.73-74.
Alexandra Berzon: Jobs’s biological father: Reunion never came. The Wall Street Journal Asia, Oct.11, 2011, pp. 1, 14-15.
Andy Crouch: The Secular Prophet. The Wall Street Journal Asia, Oct.7-9, 2011, p. 18.
Lev Grossman and Harry McCracken: The inventor of the Future. Time, Oct.17, 2011, pp.42-50.
David Gelernter: Bringing You the coolest show on Earth. The Wall Street Journal Asia, Oct.7-9, 2011, p. 16.
Yukari Iwatani Kane and Geoffrey A. Fowler: Steven Paul Jobs, 1955-2011 – Apple co-founder transformed global technology, media and retailing. The Wall Street Journal Asia, Oct.7-9, 2011, pp.1,13, 14.
Leander Kahney: Inside Steve’s Brain, Atlantic Books, London, 2008. 294pp.
John Markoff: Game changer who went beyond gadgets: Jobs altered the ways we use technology. International Herald Tribune and New York Times, Oct.7, 2011 (more than one complete print page long obituary)
Jack Schofield: Steve Jobs obituary. The Guardian (London), Oct.6, 2011.
David Streitfeld: A Silicon Valley chief like no other. International Herald Tribune, Oct.8-9, 2011, p.14.
*****
And there are at least FOUR LEVELS OF SOFTWARE TRACKING GOOGLE/ANDROID PHONES, and at least FIVE LEVELS OF SOFTWARE FOR TRACKING YOU VIA THE APPLE COMPUTER CORPORATION--whether on the iPhone, iPad, or through iTunes--known to secretly track you, and all failing to let you know that it does as well.
Apple corporation has a 'no comment' on all these stories--EXCEPT one related to external application from Twitter. On one of these security holes, Apple left it unresolved for three years so third-party hackers (known to be government agents, see below) could continue to exploit it to read anything on your computer proper as well).
Google-based phones innately spy on you now, based on Google's updated (non)privacy arrangements that will be enforced by March 2012.
So all those over precious iPhones track you without your knowledge just like Google/Android phones do as well:
#1 TRACKER ON THE IPHONE (AND ON AND ABOUT GOOGLE/ANDROID AND MICROSOFT PHONE 7]
Apple location row exposes smartphones as double agents
Smartphone makers are presenting users with a dilemma over privacy and location services.
Photo: Getty
By Christopher Williams, Technology Correspondent8:00AM BST 30 Apr 2011 8 Comments
According to Steve Jobs, Apple’s mercurial chief executive, the controversy of the last two weeks over the way the iPhone has been quietly logging users’ movements was the result of a software “bug” and public misunderstanding. [translation: Steve Jobs is head bullsh**ting artist]
But the attention garnered by the issue means that despite the deployment of Mr Jobs’ famed “reality distortion field” – the facetious term given in technology circles to his uncanny ability to deflect criticism – many more smartphone owners understand that the device in their pocket can act as a double agent. As well as delivering information to them, it can collect information about them.
Mr Jobs was responding to the work of two British researchers, Alisdair Allen and Pete Warden. Tinkering with their iPhones’ mapping capabilities, they found a log file that contained coordinates based on which mobile phone masts are nearest, along with time stamps, allowing them to plot their own movements going back a year.
Such a record, stored on both the iPhone and its associated computer, would be invaluable to a jealous spouse or a snooping employer. It was quickly found the data was also being sent back to Apple.
In the privacy firestorm that broke out as soon as Mr Allen and Mr Warden reported their findings on the web, it emerged that specialist digital forensics textbooks had already documented the location log and advised investigators on how to exploit it.
RELATED ARTICLES
Apple promises fix for iPhone tracking 'bug' 28 Apr 2011
iPhone 'tracks users' locations' 20 Apr 2011
Pressure to explain iPhone tracker 21 Apr 2011
Attention quickly turned to other popular smartphone operating systems.
Sure enough, Google Android devices were found to be sniffing out WiFi networks as their owners wander the streets and storing their locations, albeit for a shorter period than the iPhone.
Android handsets also report the data back to Google, and crucially transmit a unique identifier, so the database effectively knows where each user has been and when. From this it would be a simple matter to work out where one lives or works.
Similarly, it emerged that Microsoft Windows Phone 7 handsets send back packages of WiFi and mobile mast location data to headquarters. They do not store a log on the device, but do include a unique device identifier in their frequent dispatches.
Many ordinary users greeted these revelations with shock, but as evidenced by the textbooks that predated the controversy, police and intelligence agencies were way ahead of them.
British police are now trained to seek out smartphones immediately when they seize belongings. In the past, fingerprints might have been the first forensic priority but today it is the digital traces everyone leaves that investigators seek first. There are few things more helpful to a detective than a complete record of a suspect’s movements – and most smartphones can provide exactly that.
Nevertheless, the main reason why the smartphone firms are collecting WiFi and mobile mast locations centrally is benign [nonsense: that is called "plausible deniability". Look it up.]. A device using GPS alone can take several minutes to pinpoint its location reliably, but one with access to a database of local wireless networks can do it in seconds. Mapping functions or apps that find you a good restaurant nearby are faster and more accurate as a result.
While Apple insists its records are anonymised, according to Professor Ross Anderson, of the University of Cambridge Computer Laboratory, that doesn’t mean individuals cannot be tracked by a determined snooper.
“Anyone who knows where you were at a few definite times in the past can identify your location history from among all the millions of other people’s, and then work out where you were at, say, evenings and weekends,” he explains.
As well as the threat to privacy from location data, campaigners also worry about how it could be exploited commercially. Knowledge of where you’ve been could be very valuable to, say, an advertiser hoping to target you with tailored offers or perhaps more disturbingly, an insurance company checking where you park your car.
The question of whether users are giving full consent for their location to be tracked and used is central to the debate. Few read complex and legalistic smartphone privacy policies, and Apple admitted that it had logged the location of even those who had opted out, blaming a “bug”. [A 'bug' of course is slang for an intelligence operation that plants technology to spy on and to track people's phone conversations or location.]
For Steve Jobs the issue is simple however: hand over your location data or severely limit your iPhone’s capabilities.
“If people don’t want to participate in things, they will be able to turn location services off,” he told journalists this week. [Though it was revealed several months later this was disingenuous, because there was a SECOND SECRET level of data logging. Keep reading.]
---
http://www.telegraph.co.uk/technology/mobile-phones/8483920/Apple-location-row-exposes-smartphones-as-double-agents.html
#2 TRACKER IN THE IPHONE [AND IPAD]
The image above [at the link] shows an iPhone user’s location during travel from New York to Washington.
From the NY Times Bits blog:
“The file, which is called “consolidated.db,” keeps track of GPS data on 3G-enabled Apple devices and regularly updates itself with a user’s location. The image above shows data collected from a single trip between New York City and Washington.
Information that is stored on the phone is also sent to the iTunes application when a user syncs or backs up an iPhone or 3G iPad.
In a blog post on the O’Reilly Radar Web site, Mr. Allan said, “The presence of this data on your iPhone, your iPad, and your backups has security and privacy implications.” The two programmers have contacted Apple’s product security team but said they had not yet had a response.
Apple has also not responded to a request for comment from The New York Times.”
You can download the iPhone Tracker app here. It will show you the data that has been tracked on your iPhone4 by Apple.
“This open-source application maps the information that your iPhone is recording about your movements. It doesn’t record anything itself, it only displays files that are already hidden on your computer.”
http://www.north.com/latest/apple-secretly-tracks-your-iphone-4-locations/
#2 TRACKING SOFTWARE ON THE GOOGLE/ANDROID PHONES
And of course it comes full circle with Google/Android phones secretly tracking people as well as Apple though a SECOND arrangement it seems:
Software on Android phones 'tracking every key stroke'
Software installed on millions of Android phones is thought to be secretly tracking every key stroke, Google search, and text message by their users, it has been claimed.
By Katherine Rushton, Media, Technology and Telecoms Editor10:30PM GMT 30 Nov 2011
An Android app developer in America has posted a video showing what he claims is 'conclusive proof' that 'Carrier IQ' software installed by manufacturers of many US [Android/Google based] phones record the way those phone are used in real time, as well as their geographic locations.
Carrier IQ has claimed that the software only tracks information for the benefit of users, not for any spying purposes, and that it is “counting and summarising” information rather than recording it.
However, in a YouTube video posted on Monday, the developer, Trevor Eckhart, did a “factory reset” on his Android phone, returning it to the condition in which it is shipped to customers, and linked it to a computer screen which allegedly displayed what the Carrier IQ software was tracking.
The demonstration showed that the software read every keystroke put into the phone, as well as every text message sent to it. It also appeared to log location data, and transmit this [across the Internet out of the cell phone] to Carrier IQ.
Mr Eckhart, claims it is used by manufacturers of phones that use Google's Android operating system, as well as some BlackBerry and Nokia handsets. It is not thought to be used in Apple’s iPhones. [Wrong: within a week or two it was found on Apple iPhone's as well. See below.]
It is not known if Carrier IQ is in use in Europe, where it might present a serious breach of the Data Protection laws.
A source at a leading mobile operator said his company didn't install it but that he had been investigating whether UK manufacturers had done so and “couldn’t give a definitive answer”.
Carrier IQ said in a statement that it “assists operators and device manufacturers in delivering high quality products and services to their customers … by counting and measuring operational information in mobile devices – feature phones, smartphones and tablets.
“The information gathered by Carrier IQ is done so for the exclusive use of that customer, [lie: because the data was being hidden and is not "for the use of that customer"] and Carrier IQ does not sell personal subscriber information to third parties,” it added.
Carrier IQ would not return requests for further comment, but according to US reports it has issued Mr Eckhart with an order to take down its video. There is no suggestion that Google has authorised the use of the Carrier IQ technology.
---
http://www.telegraph.co.uk/technology/mobile-phones/8927164/Software-on-Android-phones-tracking-every-key-stroke.html
#3 TRACKING SOFTWARE ON THE IPHONES AND IPADS
Apple iPhone linked to Carrier IQ 'spyware'
References to controversial software that can be used to monitor almost everything a user does have been uncovered in Apple’s iOS operating system for the iPhone. Carrier IQ says it is 'the leading provider of mobile service intelligence solutions'
11:48AM GMT 01 Dec 2011 / 9 Comments
Carrier IQ’s software is sold to mobile operators as a way of monitoring how their networks are used but it has been labelled as "spyware" by critics. It had previously been found in Android handsets issued by American operators and shown to be capable of logging users' key strokes.
According to a well-known iOS hacker, “chpwn”, references to the software are also present in version 3, 4 and 5 of Apple’s mobile operating system.
Under normal circumstances it appears to be switched off, however, and unlike in Android devices it does not seem to be allowed to log users’ texts or other data they enter.
“I am reasonably sure it has no access to typed text, web history, passwords, browsing history, or text messages, and as such is not sending any of this data remotely,” chpwn wrote.
The disclosure has nonetheless concerned iPhone users. Carrier IQ is embroiled in a major privacy controversy in the United States, where it has been revealed that its software is routinely installed on Android handsets issued by the Sprint network.
Chpwn said the version of Carrier IQ's software, if enabled, would be capable of reporting back details of an iPhone user's phone number, calls made (though not number dialled) and location to their mobile operator.
Apple did not immediately respond to an email requesting comment.
Discussing Carrier IQ software on Android devices, Graham Cluley of the internet security firm Sophos said: "The inability to opt-out or remove the software without informing the user is extremely concerning.
"Combine that with all of the sensitive information the software is designed to intercept and it raises far more questions about how this software is being used."
---
http://www.telegraph.co.uk/technology/apple/8928053/Apple-iPhone-linked-to-Carrier-IQ-spyware.html
All the denials about embedded digital spying on phones is getting unbelievable now:
FBI Used Data From Cell Phone Tracking App 'Carrier IQ': Denies FOIA information request
Dec 13, 2011
1:34 min.
The FBI has denied a request for more details about how the agency might be using Carrier IQ, according to a blogger who filed a Freedom of Information Act (FOIA) request for data.
Carrier IQ, meanwhile, released a lengthy FAQ today in which it explained its technology and once again denied logging keystrokes or improperly collecting user data.
For those who need a refresher, Carrier IQ made headlines in recent weeks after a researcher, Trevor Eckhart, suggested that the technology is secretly embedded on many popular phones and can gather personal data about users. Carrier IQ said its technology is used for diagnostic purposes and denied logging keystrokes or being able to read the content of emails, text messages, or Web sites.
In the wake of the controversy surrounding the company, Michael Morisy of Muckrock News filed a FOIA request for "manuals, documents or other written guidance used to access or analyze data gathered by programs developed or deployed by Carrier IQ." But on Dec. 7, the FBI denied that request, arguing that the records in question were related to "a pending or prospective law enforcement proceeding," and their release might "interfere with the enforcement proceedings."
...
---
http://www.youtube.com/watch?v=ZUFS4ChL6oc&feature=related
#3 TRACKER FOR GOOGLE/ANDROID PHONES: GOOGLE'S UPDATED (NON)PRIVACY POLICY REQUIRES YOU TO LET GOOGLE LOG (SPY ON) YOUR PHONE CALLS
Now Google requires you, if you own a Google/Android Based Phone to allow them to spy on all your phone calls--'from' and 'to' issues:
Google To Track All Your Android-Based Phone Calls--Collated with Everything Google
2:04 min
Google lies and calls it a 'privacy' policy, when as the newscaster says they might as well call it a "unprivacy policy" since Google takes the right to put your data anywhere in the world it wants and has the right to collate all your phone calls in its databases.
#4 TRACKING SOFTWARE VIA APPLE: ITUNES HACK, EXPLOITED BY GOVERNMENTS FOR YEARS, AND LEFT 'UNFIXED' BY APPLE FOR 3 YEARS
In the web based software world, Apple iTunes website is as huge as Google. And the ITunes website was an open door for many years for governmental surveillance. The iTunes software program was a hacker program:
Apple iTunes flaw [sic?] 'allowed government spying for 3 years'
An unpatched security flaw in Apple’s iTunes software allowed intelligence agencies and police to hack into users’ computers for more than three years, it’s claimed.
Apple's iTunes software is installed on more than a quarter of a billion computers Photo: GETTY
By Christopher Williams, Technology Correpsondent1:27PM GMT 24 Nov 2011 104 Comments
A British company called Gamma International marketed hacking software to governments that exploited the vulnerability via a bogus update to iTunes, Apple's media player, which is installed on more than 250 million machines worldwide.
The hacking software, FinFisher, is used to spy on intelligence targets’ computers. It is known to be used by British agencies and earlier this year records were discovered in abandoned offices of that showed it had been offered to Egypt’s feared secret police.
Apple was informed about the relevant flaw in iTunes in 2008, according to Brian Krebs, a security writer, but did not patch the software [until THREE YEARS LATER, IN 2011, I.E., APPLE WAS IN CAHOOTS WITH MAINTAINING THE SPYING PROJECT] until earlier this month, a delay of more than three years.
“A prominent security researcher warned Apple about this dangerous vulnerability in mid-2008, yet the company waited more than 1,200 days to fix the flaw,” he said in a blog post.
"The disclosure raises questions about whether and when Apple knew about the Trojan offering, and its timing in choosing to sew up the security hole in this ubiquitous software title."
On average Apple takes just 91 days to fix security flaws after they are disclosed, Mr Krebs wrote.
Francisco Amato, the Argentinian security researcher who warned Apple about the problem suggested that "maybe they forgot about it, or it was just on the bottom of their to-do list".
In response to reports that FinFisher targeted iTunes, Apple [hollowly] has said that it works "to find and fix any issues that could compromise systems".
"The security and privacy of our users is extremely important [sic],” a spokeswoman said. [Their actions belie this statement. They seems to want people to spy on you, otherwise, they would have fixed the issue.] This month's iTunes update 10.5.1 explained that "a man-in-the-middle attacker may offer software that appears to originate from Apple", adding that the "issue has been mitigated".
Gamma International has not commented on the matter. Registered in Winchester, the firm is one of several companies that sell computer hacking services to governments. They offer "zero day" security flaws, which have not been publicly disclosed, so attempts to exploit them are unlikely to be detected by anti-virus programs.
---
http://www.telegraph.co.uk/technology/apple/8912714/Apple-iTunes-flaw-allowed-government-spying-for-3-years.html
The more recent admission:
Now Twitter admits 'harvesting' users' [Apple and Google/Android] phone contacts without telling the owners as Apple announces crackdown
Highly private contact information is taken from smartphones and sent to remote computer
Users puzzled over why app retains contacts for 18 months
Twitter engulfed with comments from fearful users
Apple says it will stop apps taking data without users' consent
By Rob Waugh and Tamara Cohen
Last updated at 11:59 PM on 16th February 2012
Comments (48)
Share
Twitter: The site admitted that its smartphone application transmitted data from users' private address books
Twitter has admitted harvesting contact lists from its customers’ mobile phone address books without telling them.
The website said it copied lists of email addresses and phone numbers from those who used its smartphone application, amid claims it kept them on its database for 18 months.
Its management yesterday agreed to change guidance to users about what it does with their personal information, after a storm of protest from privacy campaigners in the U.S.
The breach occurs when users of the micro-blogging site click the ‘Find Friends’ option to see if any of their contacts are also on it.
Many of them did not know this meant the site then uploaded their entire address book and stored it afterwards.
Twitter spokesman Carolyn Penner said it would now offer users the option to ‘upload your address book’ or ‘import your contacts’ to make it clearer. [as if that allows them or gives them permission to spy on you now?]
She said: ‘We want to be clear and transparent in our communications with users. Along those lines, in our next app updates, which are coming soon, we are updating the language associated with Find Friends – to be more explicit.’
The practice by a giant such as Twitter raises more concerns about the privacy implications posed by social networking sites which are used by an estimated 37million Britons.
There is no suggestion the San Francisco-based firm was using the data – which it said was securely encrypted – for anything other than finding contacts for its customers.
But critics say the lack of ‘informed consent’ raises questions about other less reputable sites which could harvest details to sell on, or potentially leave customers open to identity fraud.
Jack Dorsey, executive chairman of Twitter: The company has said that it will change its apps so they make it clearer when they are transmitting and using private information
Apple iPhone 4S: The company moved to stem controversy over how apps from networks such as Twitter access, transmit and store the highly private information in users' address books
The admission also raises difficult questions for Apple, makers of the iPhone, as to why it had been allowed to happen, after the firm [lied?] said such harvesting was a violation of its policy [when it had been allowing it ALL THE TIME.].
Two American congressman wrote to Apple about the practice, prompting it to toughen measures to make sure applications did not harvest data without ‘explicit user approval’.
In a letter addressed to Apple Chief Executive Tim Cook, Representatives Henry Waxman of California and G.K. Butterfield of North Carolina, both Democrats on the House Energy and Commerce Committee, asked Apple to clarify its developer guidelines and the measures taken by the company to screen apps sold on its App Store.
Apple CEO Tim Cook: Two U.S. legislators wrote to the CEO to request information on Apple's privacy policies relating to apps which upload and transmit the information in users' address books
WHAT IS TWITTER DOING WITH YOUR CONTACT INFORMATION?
So far, Twitter has not changed the way it uses data, only amended its policy so that new versions of the app will offer a clear warning that data will be transmitted and used.
Twitter's app will still read your address book and transmit and store your data, even now.
Sites such as Twitter process data remotely on their own servers, so it's become common practice for sites to build apps which send data back to their own computers.
The data is often used to 'link' people to other friends using the service.
What has shocked users is that this highly private data is being harvested without their permission.
It's also raised issues about how companies use such private data. None of the networks involved has come clean about why they might need to store data for periods alleged to be up to 18 months - or whether they gain a commercial advantage from storing and using this information.
Instagram and Foursquare have not issued an apology, but have quietly changed their applications.
None of the companies involved has issued a full apology.
Apple's move should at least ensure more transparency for consumers about how data is used - although it's clear that social sites will continue to copy, transmit and store this data, just as Twitter has done.
The letter came after Path, a San Francisco start-up that makes a Facebook-like social networking app, attracted widespread criticism last week after a Singaporean developer discovered that Path’s iPhone app had been quietly uploading his contacts’ names and phone numbers onto Path’s servers.
The Path incident 'raises questions about whether Apple’s iOS app developer policies and practices may fall short when it comes to protecting the information of iPhone users and their contacts,' the letter said.
The legislators’ request for information cast the spotlight squarely onto Apple for the first time since an independent blogger, Dustin Curtis, wrote in a widely distributed post last week that 'there’s a quiet understanding among many iOS app developers that it is acceptable to send a user’s entire address book, without their permission to remote servers and then store it for future reference.'
Curtis blamed Apple, writing that he could not 'think of a rational reason for why Apple has not placed any protections on Address Book in iOS.'
In their letter to Apple, [U.S. Senators] Waxman and Butterfield, referenced Curtis’ blog post, adding: 'There could be some truth to these claims.'
The legislators had asked Apple to submit its response by February 29.
Apple yesterday announced [its changing nothing because it only blames the app's instead of the HUGE SECURITY HOLES IN THEIR OPERATING SYSTEM] it would now require iPhone and iPad apps to seek 'explicit approval' before accessing users’ address book data, in a bid to stem the growing storm. [red herring: getting approval to spy is hardly the issue: the issue is Apple still agreeing to share its users data with third parties, which is against Apples own surface/public policy--and illegal.]
Twitter is the latest social networking site to face a scandal over harvesting contact details, after Facebook came under fire for ‘synchronising’ users’ email address books to its site. This has since been changed.
Read more: http://www.dailymail.co.uk/sciencetech/article-2101934/Apple-moves-stop-Facebook-Twitter-accessing-iPhone-users-address-books-permission.html#ixzz1mhi5Z2uF
Concluding comment:
Carrier IQ: Researcher Trevor Eckhart Outs Creepy, Hidden App Installed On Smartphones
2:21 min.
================
Conclusion
For an open ecology on the web that demotes these monopolies and which demotes tyranny, suggested open source programs everyone should have would be Mozilla's Firefox (web browser) and Thunderbird (email client). OpenOffice (open source free version similar to Microsoft's Office Suite) is another option to cure potential surveillance grids--like those described in comments below facilitated by such a privatized communication/software network.
Linux is open source personal computer architecture to build from as well. No one should own a language. No one should own your private mail and telephone calls. Without basic senses of privacy, the idea of civil rights disappears. Civil rights are based on a premise of personal privacy against other parties, so they have to treat you as a civil equal.
Some countries are already moving over toward open source in their defense establishments because a foreign corporation with spycraft connections over their own local defense communication infrastructures is inherently misaligned.
-------------------------------
Some additional information about Facebook's founder, Zuckerberg:
The man who's made billions by selling your secrets: The Mail meets Facebook's £4.4bn founder aged 26
By David Jones
Last updated at 1:19 PM on 2nd October 2010
Worth £4.4bn at 26, Facebook's founder lives in a rented house and drives an old Honda. He's created a global network of friendships, but ruthlessly betrayed his own friends.
Forget Big Brother. [Er, why? This is an Orwellian Big Brother story.] This is the age of Big Buddy, in the unlikely form of Mark Zuckerberg, the nerdish, socially dysfunctional genius who ironically created the world’s favourite social networking website. [with huge U.S. intelligence community funding.]
An astonishing 550 million people in more than 200 countries now befriend one another on Facebook, the site he created seven years ago in his college dorm.
At 26, Zuckerberg was recently declared the youngest self-made billionaire in history. According to more than one magazine, this dentist’s son from a New York suburb is also the most influential figure on the planet — not least because much of the personal information Facebook’s users reveal is passed to advertisers, who use it to target them [or given to the U.S. security establishment?]
Since every message placed on Facebook is stored on the company’s vast computer mainframes, Zuckerberg has also been placed in a position of unimaginable power — the kind of power, incidentally, of which totalitarian tyrants could only dream.
His astonishing ascent is documented in an acclaimed new film, The Social Network, which opens in Britain this month. The big question is, should we trust a young man who has declared the age of privacy to be over — and who appears to be on some turbo-charged mission to redefine the concept of human friendship — to use this power responsibly?
Observing him this week, and talking to those who know him, he certainly seems harmless enough. Indeed, his life is remarkable only because it is so boringly ordinary. [It's hardly ordinary to go to Philips Exeter Academy, the prep school of G. H. W. Bush, and then off to Harvard.]
Despite being worth a staggering £4.4 billion, he has no interest in mansions, fast cars, parties and model girlfriends, and is said to be only truly at ease when gazing into a computer screen.
Zuckerberg lives in a rented four-bedroom house in a quiet cul-de-sac in the U.S. computer industry capital of Palo Alto, California.
He has been there for around a year and, though it is an ordinary, middle-class street, by sheer coincidence, one of the inventors of [Google Owned] YouTube lives in an equally modest home next door.
Zuckerberg recently placed a note on the windscreen of another neighbour’s battered, 35-year-old BMW, asking whether it was for sale. His offer was rejected, so he continues to drive the sort of Honda saloon car handed out to sales reps.
According to one woman on the street, he is an ‘ill-mannered dork’, for she claims that when her 83-year-old mother bade him good morning, he ignored her.
But others say he is friendly enough, and Andrea Barlas, a marriage guidance counsellor who lives nextdoor but one, told me she was hoping to match him up with her 17-year-old daughter Alie.
She was joking, but in any case Zuckerberg is spoken for. His long-term girlfriend Priscilla Chan, a Chinese-American student paediatrician, moved in with him this month.
Inevitably, this momentous event was marked with a folksy message to his Facebook friends (he lists 879 of them): ‘Now we have 2x everything, so if you need any household appliances, dishes, glasses etc, please come by and take them before we give them away,’
Last Wednesday was another typical day in Zuckerberg’s life, although for me it was the chance to meet an icon of the modern world.
If he had bothered to record our encounter on his Facebook page, I suspect this is what he might have written: ‘Another sunny day in Silicon Valley — so I walked the few blocks to the office.
‘On the way, I met this guy from the Daily Mail. He said he was a reporter and he’d flown all the way from London to California just to meet me! Wow!
‘I posed for a photo with him and made polite conversation, but told him I was far too shy — and busy thinking about my upcoming business meeting — to talk for very long.’
What’s certain is that after our brief encounter, Zuckerberg began another 16-hour day at the Facebook HQ; an anonymous modern building half a mile from his house.
He does not recline in a well-appointed office, but sits at a desk amid his youthful staff — techie disciples who skateboard or jog to work and wear the unofficial company uniform of trainers, T-shirt and Bermuda shorts (‘Zuck’, as they call him, prefers jeans).
If Zuckerberg felt uncomfortable when I approached him, he could hardly complain that I invaded his privacy. After all, this is the man who not so long ago declared ‘the age of privacy is dead’.
With disquieting arrogance, he also announced that when it came to personal confidentiality, his website was setting a new ‘social norm’.
Picture: Mark walking to the facebook offices near his Palo Alto home wearing jeans to work
Moreover, there is just a suspicion that Zuckerberg’s unaffected, geeky image has been cultivated to chime with his vision of a sharing, open society [with deep vampirish teeth sunk into it's neck from the U.S. intelligence apparatus funding arrangement from the start.]
He may appear awkward and ill-at-ease, but there is a ruthless streak — for Zuckerberg is a man with a mission.
He dreams of a world when every man and woman on earth is connected via Facebook and his website serves as their social club, noticeboard and computerised confessional.
Watching the new film about him this week, one had to wonder whether he is the right character to control such a world.
In The Social Network, which is expected to contend for Oscars, Zuckerberg is portrayed by Jesse Eisenberg: a slightly built, tousle-haired young actor who resembles him strongly and comes from the same middle-class, New York Jewish background.
The film portrays Zuckerberg as trapped by his own massive IQ, as someone who finds it so difficult to form close relationships and empathise with others that, at times, he seems to border on the autistic.
More disconcertingly, he is portrayed as an amoral, remorselessly ambitious young man who is prepared to betray his one true friend to ensure Facebook’s success.
Based on a purportedly factual novel called The Accidental Billionaires, the story takes us back to Harvard in late 2003.
Then a 19-year-old computer science undergraduate who had already designed various innovative websites, Zuckerberg had just been rejected by a girl he was courting.
For all his brilliance, he was also acutely aware he would always be an upstart in the eyes of the wealthy elite WASPs (White Anglo Saxon Protesants) who held sway at Harvard.
Drunk and embittered, Zuckerberg created a crudely sexist website in which he juxtaposed the photographs of female students [with farm animals mixed in] and invited users to vote which one was ‘hottest’.
As he purloined the pictures by hacking into computerised college yearbooks — known at Harvard as facebooks — he called his site ‘ facemash’.
It proved so popular that within hours the entire university computer system had crashed.
But in the hallowed halls of America’s leading educational institution it caused outrage, and Zuckerberg was hauled before a disciplinary committee. He escaped expulsion by apologising, but was placed on probation.
However, his notoriety brought him to the attention of Tyler and Cameron Winklevoss, 6ft 5in identical twins who starred in the university’s rowing team and later represented the U.S. at the Beijing Olympics.
Picture: Twin brothers Tyler and Cameron Winklevoss, who launched a multi-million dollar lawsuit against Mark Zuckerberg
Eager to follow their wealthy father into business, they had come up with the idea for a new dating website, exclusively for Harvard students, and needed someone to write the computer code. Who better than the ace hacker behind facemash?
All this is true and undisputed. The story of what happened next is much muddier and Zuckerberg is still embroiled in a legal wrangle with the Winklevoss twins to this day. The story left out the other person, an Indian, who was the go-between who had a 'facebook' idea that some argue Zuckerberg stole when he was contacted by the go-between to make the Winklevoss's website.]
If we believe the brothers, he shamelessly stole their concept, refined it and turned it into thefacebook.com (the prefix was dropped later).
It went live in February 2004 and spread with viral speed to hundreds more colleges and universities across America. [U.S. In-Q-Tel spycraft funding arrived in 2004 for the first time as well.]
That summer, Zuckerberg dropped out of Harvard and moved to Silicon Valley, where his heroes such as Microsoft’s Bill Gates and Apple’s Steve Jobs had made their fortunes.
Several college friends followed him. Dossing on mattresses in a cheap rented house, they worked night and day on the site, adding new features and opening it to everyone, not only college kids.
A rich venture capitalist [with neoconservative and CIA connections, Thiel] provided the funds Zuckerberg needed to expand — and the rest is history [well, whitewashed history with this bracket of very important information left out]. Today, his company employs 1,700 people, has offices all over the world and is valued at £20 billion.
Yet Tyler Winklevoss claims he is unfit to run it. ‘In my experience, he is clearly amoral and non-ethical from top to bottom,’ he told me this week. ‘We had an agreement and he totally misled us. I don’t think he should be trusted with anything. That’s what’s so scary about it.’
In an out-of-court settlement two years ago, Facebook agreed to pay the twins a reported £43 million, but they are now appealing against this, claiming the company was over-valued at the time, so the shares they were awarded are not worth as much as they were promised.
They are determined to force Zuckerberg into court, and if they succeed their lawyers will doubtless highlight a series of emails he sent during the website’s creation.
For many years the emails remained secret, but they were recently leaked to the website Silicon Alley Insider.
Asked by one friend what he intends to do about the Winklevoss brothers, he recklessly states his intention to: ‘F*** them . . . probably in the ear.’
'He never lets anyone forget Facebook is his show'
Given that Zuckerberg now has access to the highly personal musings of half a billion people, another email exchange is even more disturbing.
‘Yeah, so if you ever need info about anyone at Harvard . . . just ask,’ he boasts to his friend. ‘I have over 4,000 emails, pictures, addresses . . .’
Friend: ‘What!? how’d you manage that one?’
Zuckerberg: ‘People just submitted it . . . they trust me . . . dumb f***s’
Zuckerberg strongly denies stealing the Winklevosses’ idea, insisting he was already forming plans for his own, radically different social networking site when they approached him.
And, as he points out, these emails were sent out seven years ago by a gauche 19-year-old student, not the head of a multibillion-dollar company.
Indeed, a few weeks ago, when a New Yorker magazine reporter questioned him about them, Zuckerberg sounded chastened and embarrassed. ‘I think I’ve grown up and learned a lot,’ he said.
Certainly, in Silicon Valley the consensus is that he is fast developing into a savvy and astute corporate chief.
Yet some critics question whether, deep down, his regard for people’s confidentiality has really changed that much.
This question becomes more uncomfortable when it is linked to Facebook’s ever-shifting privacy policy, which continues to be the centre of controversy.
Then there is Zuckerberg’s curious attitude towards friendship — the value that underpins his website. At Harvard, his one real friend was Eduardo Saverin, who hailed from a wealthy Brazilian Jewish family.
While Zuckerberg was the engineer behind the Facebook project, Saverin was the business brain.
An economist who made £200,000 from share trading while still at university, he funded the website in its early days.
When Zuckerberg decamped to California, however, his partner opted to remain in New York to try to raise advertising revenue. Soon afterwards, he was frozen out of the company — for in California, Zuckerberg had found a more influential new sidekick.
He was Sean Parker, the slick operator behind the now defunct pirate music website Napster.
In the film, the louche Parker (played by pop star Justin Timberlake) impresses Zuckerberg by introducing him to a lifestyle that had always seemed beyond him; a world of fancy restaurants, high-octane parties and beautiful women.
The geek can hardly believe his luck as a beautiful lingerie model flaunts her charms in his direction, in a San Francisco fleshpot.
What happened next is left to our imagination, but according to Ben Mezrich, author of The Accidental Billionaires, this scene is authentic.
‘I know that they left the club together, but after that I have no idea,’ he says.
But back to Eduardo Saverin. Stunned by the way he was discarded, he sued, and in yet another out-of-court settlement, he received a reported £750 million.
His name has also been reinstated in the list of founders on Facebook’s website — but it is highly unlikely he is among Mark Zuckerberg’s many Facebook friends.
‘All his friends from the early days have gone,’ says Nicholas Carlson, the Silicon Alley Insider’s deputy editor. ‘He may have no social skills, but don’t be deceived — he’s cut-throat and he never lets anyone forget that Facebook is his show.’
So will The Social Network harm Zuckerberg’s reputation and that of his cherished creation?
Certainly his PR advisers appear to fear as much. This week, he trumped the film’s U.S. release by going on the Oprah Winfrey show to announce he is to
donate $100 million (£63 million) to an educational project for disadvantaged children, yet his largesse was interpreted as a damage limitation exercise.
In a strange way, however, I think the movie lends Zuckerberg a certain allure. Yes, he comes across as dorkish and emotionally stilted, but he is the super-brainy outcast fighting the might of the East Coast establishment.
He is also scripted with a razor-sharp wit (which those who know him say he doesn’t really possess) and, in the end, we feel rather sorry for him.
None of this concerns him, he insists. For, as he told me, he has no intention of watching the film that will complete his extraordinary transformation from faceless nerd to instantly recognisable celebrity.
And whatever people might make of Facebook’s eccentric founder, half a billion users speak for themselves.
The age when friendships are formed in cyberspace and privacy is dead — Mark Zuckerberg’s startling ‘new social norm’ looks set to stay.
Read more: http://www.dailymail.co.uk/news/article-1316959/The-man-whos-billions-seeling-secrets-The-Mail-meets-Facebooks-4-4bn-founder-aged-26.html#ixzz11IZcBn58
3 comments:
related books:
'Jacquard's Web : How a Hand-Loom Led to the Birth of the Information Age ' [effectively software, via punch cards]
'The Bride of Science: Romance, Reason, and Byron's Daughter'
'The Turk : The Life and Times of the Famous Eighteenth-Century Chess-Playing Machine'
'The Difference Engine : Charles Babbage and the Quest to Build the First Computer' [effectively "hardwired software"--software is the hardware, physically resettable ('reprogrammable') for different mathematical operations]
'IBM and the Holocaust: The Strategic Alliance between Nazi Germany and America's Most Powerful Corporation' [tailor made "hardwired software" programs, via punch cards, Nazi Germany's tailor desired--and IBM tailor made--tabulation machines are the earlier source of all of the WWII era software conceptualization...]
'Dealers of Lightning : Xerox PARC and the Dawn of the Computer Age'
'From Airline Reservations to Sonic the Hedgehog : A History of the Software Industry (History of Computing)'
Recommendations here are:
open source operating systems for computers; private (i.e., secret) operating systems for mass public computer operating systems are only a recipe for technological fascism and a police state--as Microsoft already has "Homeland Security" contracts to (what else?) spy on everyone through its software...
1. Microsoft's Endless Internet Explorer Holes and their Department of Homeland Security Contract * http://www.rense.com/general70/exploi.htm
2. Microsoft Helps China Censor Bloggers, by Jonathan Watts in Beijing
The Guardian - UK, 6-15-2005
3. Microsoft's Really Hidden Files * http://www.elizabethmustdie.com/h4x04txt/IE5HiddenFiles.htm
4. Evidence For The Microsoft WinXP Pro Bugging Device, by Mike McCarron * http://portland.indymedia.org/en/2004/10/298876.shtml
5. How NSA Access Was Built Into Windows, by Mortose-Mortland * http://www.totse.com/en/politics/national_security_agency/hownsaaccesswa168922.html
6. "Congressman from Microsoft Corp.'s home state was criticized by the chairman of a House technology committee for an attack on the free software movement...", D. Ian Hopper, AP Technology Writer 3:45pm Thu Oct 24 '02 and here http://www.informationweek.com/story/IWK20021024S0001
7. "Security Report Puts Blame On Microsoft," Washington Post, September 24, 2003
"Schneier said the problem with Microsoft is that it is so intent on being dominant that it designs its systems primarily to keep out competitors, not intruders. "Their goal is to facilitate lock-in" of Microsoft products, he said. here http://www.bizreport.com/news/5003/
8. "Microsoft's 'Trusted Computing' makes Bill Gates the lord of your computer,"
by Jason Haas; here http://madison.indymedia.org/newswire/display_any/6637
9. "Microsoft Corp. warned Asian governments Thursday they could face patent lawsuits for using the Linux operating system instead of its Windows software. The growing popularity of Linux -- an open-source software that is freely available on the Internet and easily modified by users -- is a threat to the global dominance of Microsoft's Windows." here http://www.msnbc.msn.com/id/6522431/or here http://portland.indymedia.org/en/2004/11/304065.shtml
10. "Warning: Microsoft 'Monoculture', AP, "Dan Geer lost his job, but gained his audience. The very idea that got the computer security expert fired has sparked serious debate in information technology. The idea, borrowed from biology, is that Microsoft has nurtured a software "monoculture" that threatens global computer security. Geer and others believe Microsoft's software is so dangerously pervasive that a virus capable of exploiting even a single flaw in its operating systems could wreak havoc. Just this past week, Microsoft warned customers about security problems that independent experts called among the most serious yet disclosed. Network administrators could only hope users would download the latest patch. After he argued in a paper published last fall that the monoculture amplifies online threats, Geer was fired by security firm @stake, which has had Microsoft as a major client. Geer insists there's been a silver lining to his dismissal. Once it was discussed on Slashdot and other online forums, the debate about Microsoft's ubiquity gained in prominence...." more here
http://www.wired.com/news/privacy/0,1848,62307,00.html
Defective Software Engineering
The Invisible Source Of Countless Headaches
By Ted Twietmeyer
8-16-5
We have all taken a clenched fist to a computer at one time in our lives (and it hurt.) It's time to ask - must it always be this way? Must printer and peripheral manufacturers ship product with known defective driver disks - forcing us to head for their website while the power cord is still in the box?
UNDERSTANDING WHAT SOFTWARE IS
This short section is intended to help non-technical readers to quickly get up to speed. If you are someone involved in electronics or software engineering, skip to the following section.
(LEFT) - Jacquard looms made in 1801 used punched cards on folding loops to weave patterns. These cards allow you to see what a weaving "program looks like. The IBM punch cards of the last century are essentially the descendents of these giant loom cards. Any program can only execute one instruction at a time, just like the Jacquard loom machine does. The loom used "fingers that would "feel for the holes, thereby controlling the weaving mechanism and which colored threads would be woven.
Lay people and some car mechanics often refer to the microprocessor in your car and appliances as the "brain. In reality, it isn't even as a smart as a grasshopper.
Software can be divided into two categories, and the line between these two categories is beginning to blur:
1. Firmware "Firm implies programming which is not lost or erased when the product is turned off. Electronic products like video players, televisions, appliances, traffic light equipment and motor vehicles of all kinds have firmware. This is software permanently stored in memory, which the customer never cares about, loads or changes. In computers this is known as the BIOS. It can be updated, but rarely is nowadays. Firmware is also widely known as "embedded code.
2. Software "Soft describes its volatility to power loss quite well. The program is lost when power is turned off. Your personal computer uses this. The operating system is loaded from your hard drive at power up, or whenever you launch a program.
Computers have a small amount of firmware which makes it possible to automatically run and load Windows or the Mac operating system after power is switched on. Some of the simplest and most clever firmware programs are those hidden inside toys, bread machines, exercise equipment, watches and much more. More complex programs operate heavy equipment like cranes, spacecraft, ships, tanks, missiles and more.
I have programmed microprocessors since they first came out back in the mid 70's. And I've watched how the industry has handled advancements in the technology of compilers, which actually create the code (or program) executed by the hardware. The first microprocessors were literally hand-coded on paper one memory location at a time. Then the binary instruction codes were entered into a keypad for programming into permanent memory. Each memory location can be thought of as equivalent to each card in the loom you above. Hand coding is a painfully long process, that leaves little time to add any extra user features, like simpler user interfaces. These came later when compilers were created to write firmware.
We all know about the cryptic, bizarre and endless different methods by which VCRs, DVD players and microwave ovens must be set by the user. There are probably more flashing VCR and microwave oven displays in America than there are traffic lights. This is the legacy of owners who gave up trying to set the time. One would think manufacturers would catch on to the problemespecially after more than 30 years of building countless microprocessor controlled consumer appliances.
SOFTWARE ENGINEERING IS MOSTLY A MINDSET - NOT A METHOD
A good example of this is the Williamsburg Bridge over the East River, in New York City. A shortcut was taken by not using galvanized steel wire in the suspension cables. In just a few years, the city was faced with a major expenditure to repair it.
Shortcuts are taken in engineering far too often, just to save a buck. Automobile recalls are often the result of shortcuts or just plain bad engineering. These create safety hazards and result in recalls that cost far more than doing it right in the first place.
Under Daniel Goldin, NASA personnel were hammered relentlessly with his mantra "better-faster-cheaper. When you send a vehicle 40 million miles into space, you cannot take shortcuts. As a result of doing so, missions were lost as well as the agency's long-standing credibility. These failures almost cost the agency future manned missions, as Congress grew angry.
Penny pinching with any engineering profession is a tricky business, as it is with software and firmware. Tools were created to "manage software development. In essence this is like scheduling creativity. Imagine trying to rush an artist or composer - you can guess what the end result will be. You will get about the same results as a woman will get, when attempting to put lipstick on in a car while traveling over a dirt road.
All this leads us to the headaches buried in electronic products. Detroit won't tell you when they have made "software upgrades to engine and transmission controllers. All of these boxes use one or more microprocessors. Instead, a mechanic may tell you "the computer module is bad, and needs replacement. Exchange is $400.00 + 200.00 labor to reach it. There is a company outside of Harrisburg, PA. one of my relatives works at. They have made millions of dollars over the years assembling and programming engine, transmission and body modules.
Like a contract between two people that is only as good as those who sign it, the same is true with both firmware and software design. There is an invisible contract between a programmer and a product. ANY product, no matter how well it appears or how careful it is mechanically constructed, will only be as good as the microprocessor code that makes it function. And subsequently, the diligence of the person(s) writing the code will determine product reliability. Remember those VCRs and microwaves?
TOOLS THAT SOFTWARE ENGINEERS USE
Those outside of the profession are often unaware of these tools. These tools are called compilers, and are used by firmware and software engineers to compile high level languages into low level code. Compilers handle level languages like C, C++, C#, BASIC, Java or others. These tools create the final machine code the microprocessor will actually run to perform the intended useful task.
Another source of the problem in recent years has been Microsoft. Just a few years ago, languages like BASIC and C were very different from each other. They were also simple to learn and use. Now the line between languages has blurred. Microsoft has moved everything into what they call the .NET format, which is supposed to provide simple connections to the internet. This incredibly complex paradigm they have created has resulted in LONGER time to market, not shorter. With today's compiler packages, they provide several BIG wall charts. These white-board-size color prints are far too large to unfold by one person and hold up to read. There are more than a thousand pre-defined functions, classes and variables. These giant charts also have printing on BOTH sides. How is a programmer supposed to KNOW which side is less important when they hang it on the wall? And will he/she have enough wall space for 10 of these?
Because of this utterly absurd added complexity, today's programmer is now more insulated from the hardware than ever before. Now programmers have very little idea what is really going on in any computer for which they have written a program for. Debugging code now has become a guessing game. Testing for undesirable interactivity between various programs from other companies has become almost impossible. Violate just one of Microsoft's endless programming rules and all bets are off for functionality, reliability or compatibility.
FIRMWARE
This is a VERY different discipline from writing regular software. A programmer has complete and intimate control of the hardware with firmware. I know several regular computer software engineers, that cannot mentally relate to writing code that directly controls hardware. In a home computer, the operating system watches your mouse or keyboard for your input.
For a bread machine, the programmer must write code to read the pushbuttons, time the cooking cycle, and display current time and cooking information. In a vehicle, the programmer must write code that directly monitors engine sensors, switches, buttons and body sensors while controlling numerous lamps, displays, valves, solenoids, gauges and indicators. The control equations and algorithms are fairly straight forward for accomplishing this. Yet mistakes are still made, and something highly unexpected can occur without warning. This is because current software testing methodology attempts to find all the obvious problems, verifies the programming meets intended operational requirements. The testing inherently assumes that a programmer is diligent and writes code using common sense.
COMMON SENSE ENGINEERING
The real problem in all engineering fields? No one can teach engineers common sense. For example, think about the Ford Taurus front car door. As you open the door, the corner of the door barely misses your eye. Yet this foolish body design went on for years. No recall was ever made, because Ford would have to give people a new car to fix it. Yet people kept buying them, so Ford kept making them. This is a good example of how people encourage bad design to continue. It's almost like a form of inbreeding, and it sounds like a future Edsel to me...
In the world of technical professions, there are people who have a natural talent for a given profession, and those who do not. All of us know good car mechanics - and not-so-good mechanics. It is also true in the medical profession and in engineering. In the final analysis it's not the college degree that matters, but rather how effectively you can use the knowledge you have learned.
The best engineers I've met are men and women who have taken things apart as young children (and often were not been able to re-assemble them into working order.) They have always wanted to know how everything worked. The same curiosity and diligence of understanding is also applicable to software and hardware engineers, and of those who work in aerospace. These adults today can still recall how as children they were often left in awe watching rocket launches. When NASA lost communication with the Spirit and Opportunity rovers, the mission was almost declared a total loss. To save it, NASA fetched some former engineers out of retirement to help recover the rovers, and it worked. These unsung heroes knew tricks never taught in college. I hope NASA was charged a hefty consulting fee for their work.
What this all boils down to, is that programmers must have a SENSE of responsibility. It requires aptitude and a sincere desire to write good code. A programmer cannot be primarily focused on receiving a big paycheck each month. No one can take shortcuts - regardless of whether it is a consumer product, or a space vehicle or medical equipment where lives are on the line. Space missions would have fewer problems without lost missions, personal computers would rarely crash and our vehicles would run far more reliably.
And maybe those flashing VCR and oven displays across America would eventually disappear...
Ted Twietmeyer
Dan Bricklin's Web Site: www.bricklin.com
Software That Lasts 200 Years
The structure and culture of a typical prepackaged software company is not attuned to the long-term needs of society for software that is part of its infrastructure. This essay discusses the ecosystem needed for development that better meets those needs.
I've been following some of the writings and actions of the Massachusetts State Executive Office for Administration and Finance as it deals with its Information Technology needs. It was through listening to Secretary Kriss and reading the writings he and other Massachusetts government officials have produced that I've come to look at software development from a whole new perspective.
This essay tries to present that perspective and examine some of its implications.
Many things in society are long-term
In many human endeavors, we create infrastructure to support our lives which we then rely upon for a long period of time. We have always built shelter. Throughout most of recorded history, building or buying a home was a major starting step to growing up. This building would be maintained and used after that, often for the remainder of the builder's life span and in many instances beyond. Components would be replaced as they wore out, and the design often took the wear and tear of normal living into account.
As needs changed, the house might be modified. In general, though, you thought of a house as having changes measured in decades.
Likewise, human societies also create infrastructure that are built once, then used and trusted for a long period of time. Such infrastructure includes roads, bridges, water and power distribution systems, sewers, seaports and airports, and public recreational areas. These also would be used and maintained without major modifications after they were built, often for many decades or even centuries.
Software has been short-term
By contrast, software has historically been built assuming that it will be replaced in the near future (remember the Y2K problem). Most developers observe the constant upgrading and replacement of software written before them and follow in those footsteps with their creations.
In the early days of computer software, the software was intimately connected to the hardware on which it ran, and as that hardware was replaced by new, better hardware, new software was built to go with it.
In the early days, many uses of computing power were new -- they were the first application of software to problems that were previously done manually or not at all.
The world got used to the fact that the computer version was an alternative and the special features and cost savings were what was special.
Today, hardware is capable enough that software can be written that will continue to run unmodified as hardware is changed.
Computers are no longer new alternatives to other applications -- they are the only alternative.
Despite this, old thinking and methodologies have remained.
Computers and computer software have been viewed as being valuable for no longer than common short-term durable goods like an automobile or sometimes even tires.
In accounting, common depreciation terms for software are 3 to 5 years; 10 at most. Contrast this to residential rental property which is depreciated over 27.5 years and water mains and brick walls which are depreciated over 60 years or more.
Records
Another aspect of human society is the keeping of records. Common records kept by governments include property ownership, citizenship and census information, and laws.
Personal records include images (such as portraits) and birth, death, and genealogical information. General information kept by society includes knowledge and expression, and artifacts representative of culture. Again, the time frame for keeping such records is measured in decades or centuries. I can go to city hall and find out the details of ownership relating to my house going back to when it was built in the late 1800's.
"Family bible" records go back generations. The Boston Public Library, like many city libraries, has newspapers from over 200 years ago available on microfilm, and many from the last 150 years in the original paper form.
Most of these societal records have been kept on paper.
When computers were first introduced, they were an adjunct to the "real" paper records, and paper printouts were made.
Computer-readable "backups" and transaction logs were produced and stored on removable media such as magnetic tapes, or even paper printouts. These were usually written and then rarely accessed, and even then accessed in a manner akin to the newspaper stacks of a library.
Only the recent, working copies of data were actually available to the computers on an instantaneous basis.
Much of the use of computers was for "transactions", and only the totals at the end of the time period of interest needed to be carried forward except in rare circumstances, such as disaster recovery or audits. Switching to a new computer system meant copying the totals and then switching the processing of new transactions to the new system instead of the old.
When it comes to moving ahead, most new software and hardware can only access the most recent or most popular old data. Old manuscripts created with old word processors, often archived on obsolete disk cartridges in obsolete backup formats, are almost impossible to retrieve, even though they are less than 25 years old.
The companies that built the software and hardware are often long gone and the specifications lost.
(If you are older than 30, contrast this to your own grade school compositions saved by your parents, or letters from their parents, still readable years later.)
Today's world and Societal Infrastructure Software
The world is different now than it was even just a decade or two ago.
In more and more cases, there are no paper records. People expect all information to be available at all times and for new uses, just as they expect to drive the latest vehicle over an old bridge, or fill a new high-tech water bottle from an old well's pump.
Applications need to have access to all of the records, not just summaries or the most recent.
Computers are involved in, or even control, all aspects of the running society, business, and much of our lives. What were once only bricks, pipes, and wires, now include silicon chips, disk drives, and software. The recent acquisition and operating cost and other advantages of computer-controlled systems over the manual, mechanical, or electrical designs of the past century and millennia have caused this switch.
I will call this software that forms a basis on which society and individuals build and run their lives "Societal Infrastructure Software".
This is the software that keeps our societal records, controls and monitors our physical infrastructure (from traffic lights to generating plants), and directly provides necessary non-physical aspects of society such as connectivity.
We need to start thinking about software in a way more like how we think about building bridges, dams, and sewers. What we build must last for generations without total rebuilding. This requires new thinking and new ways of organizing development.
This is especially important for governments of all sizes as well as for established, ongoing businesses and institutions.
There is so much to be built and maintained. The number of applications for software is endless and continue to grow with every advance in hardware for sensors, actuators, communications, storage, and speed. Outages and switchovers are very disruptive.
Having every part of society need to be upgraded on a yearly or even tri-yearly basis is not feasible.
rest of article:
http://www.bricklin.com/200yearsoftware.htm
Post a Comment